Symmetric vs Asymmetric Cryptography

Cryptography is a study of keeping information secret and safe by transforming it into a form that unintended recipients cannot understand.
Cryptography is broadly classified into two categories:
- Symmetric Cryptography
- Asymmetric Cryptography
Symmetric Cryptography
Let us understand symmetric cryptography with the help of an example.
Let’s say there is a sender and receiver. A sender is a person who wants to send information and a receiver is a person who receives the information. And let’s say that the sender sends “Hi Friend !!!” to the receiver.

The problem with this approach is that anyone sniffing the network can listen to the communication between the sender and the receiver. And this can be a very dangerous situation. What if the sender is sending some confidential information to the receiver? Like credit card details, ATM pin, or something.

To avoid this type of situation, the sender can encrypt the message before sending it the to receiver.
What is encryption?
Encryption is a way of scrambling data so that only authorized parties can understand the information.
And for encrypting the message sender needs a key. The sender will encrypt the information using the key.

And when the receiver will receive the information it will decrypt the information by using the same key.

Cryptography in which the same key is used for both encryption and decryption of information is called symmetric key cryptography.
Problem With Symmetric Key Cryptography
Since both the encryption and decryption keys are the same chances are very high that the key can get stolen on the way. As sender needs to send the key along with the message to the receiver so that the receiver can decrypt the information. And at that time some hacker can steal the key.

So, instead of using symmetric key cryptography what we should use is asymmetric key cryptography.
Asymmetric Key Cryptography
In asymmetric key cryptography, we have two keys:
- Public Key – This is a key that is publicly available. Just like your email address or bank account number.
- Private Key – This is a key that is private in nature. And only the authorized personnel has access to it. Like the password of your email, or atm card pin.
Any information that is encrypted/decrypted by a public key can be encrypted/decrypted by the private key. In the same way, any information encrypted/decrypted by a private key can be encrypted/decrypted by the public key.
Both the sender and receiver have their own private and public key.

The sender and the receiver exchange their public key. A public key is something that can be available to the public. So it is not a security concern.

The sender encrypts the information via the receiver’s public key. Why? Because if the sender encrypts the information using his private key in that case anyone having access to the sender’s public key will be able to decrypt the information.

Once the receiver receives the information it decrypts it using its own private key. As the information was encrypted using the receiver’s public key.

This is how asymmetric cryptography works.
Digital Signature
A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents.

In a digital signature, a message is signed by the private key of the sender. And the public key is generated by the sender’s private key.
The signature, message, and public Key of the sender are given as input to the verification function (which is present at the receiver end). If the output of the verification function is yes then the signature is valid otherwise it is not.
Cryptography In Blockchain
Cryptography is widely used in blockchain technology. Learn about Blockchain Technology here.
One of the most notable uses of cryptography is cryptographic hashing. Hashing enables immutability in the blockchain.
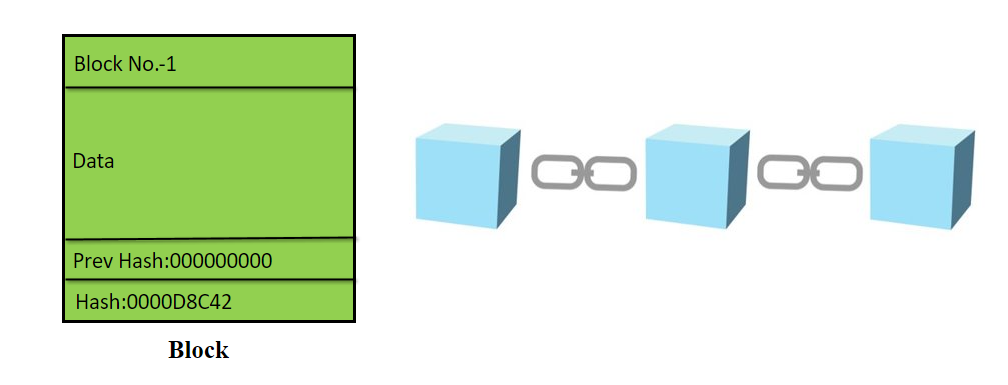
Every block in the Blockchain consists of a hash. This hash act as a unique identifier to the block. And the hash is generated by the SHA256 algorithm.
SHA256 Algorithm
Any input given to the SHA256 algorithm generates a unique hash. This algorithm is used to generate hashes in a Blockchain.

What inputs are given in case of a Blockchain to the SHA256 algorithm?
The various fields given in the block are given as input to the SHA256 algorithm to generate the hash. If you want to see this in real life click here.
For demonstration purposes, I am going to use only 8 hexadecimal characters in the Block.

Immutability In Blockchain
Immutability is what makes blockchain powerful.
Cryptographic hashes are basically used to create a link between the blocks of the blockchain.

The previous hash field of a block consists of the hash of the previous block. Blockchain number 1 is the first block of the blockchain that’s why the previous hash field is 00000000.
If some hacker tries to manipulate the data fields of any of the blocks present in the blockchain then the hash of that block will get change. Why? because as we discussed above fields of the blockchain are given as input to the SHA256 algorithm and once the fields(which act as input to the SHA256) are changed by the hacker the hash generated by the algorithm will get changed. And once a hash of a block will get changed then the other block pointing to the same block(whose hash is changed) previous hash field will get change.

And this is what makes the blockchain immutable. Any change in data can be verified and validated by the other nodes of the Blockchain.
Conclusion
So I hope by now you have understood what is cryptography, symmetric key cryptography, asymmetric key cryptography, and what are its application in the Blockchain. For any doubts or queries please comment below. Thanks for reading.
Sharing is caring
Did you like what Kshitij wrote? Thank them for their work by sharing it on social media.